by Gerald McQuaid and Domenico Raffaele Cione
[vc_row] [vc_column width=”5/6″]The ETSI work to provide a Technical Specification (TS) to support the Directive 2014/41/EU of the European Parliament and of the Council of 3 April 2014 regarding the European Investigation Order (EIO) in criminal matters [1] had started in 2016 and was carried on during all 2017 and 2018 on all technical aspects of the new interface resulting now finalized with the publication of a first version of the Inter LEMF Handover Interface (ILHI) [4]. This specification provides LEMF’s with all implementation details to allow LI data transferring from one LEMF located in the country B (responding country where a target abroad is requested to be intercepted) to a LEMF located in the country A (requesting country where the request of interception is originated).
[/vc_column][vc_column width=”1/6″]
ETSI TC LI has identified a standard LI Architecture reference model to address the new EIO requirements which impose that an LEA of a country (country A) is able to get real-time intercepted product of a target using a communication service in a CSP network located in another country (country B) in certain circumstances. The standard solution provides LI data transfer between different national borders at the LEA’s domain level without impacting the CSP interception domain implementation. The TS supported a modular approach by introducing new HI functionalities starting from the concepts of Requesting Authorized Authority (reqAA) and Responding Authorized Authority (resAA) with the corresponding Monitoring Facilities reqLEMF (in reqLEA) and resLEMF (in resLEA).
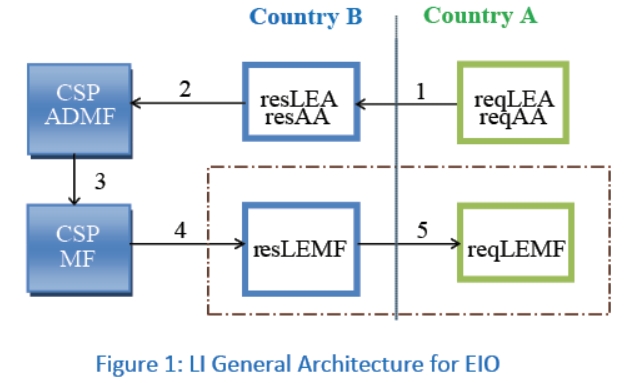
The new ETSI Architecture standard model for EIO is shown in Figure 1 which introduces five different interfaces steps:
The requesting LEA or AA sends a message in accordance with EIO [1] to responding LEA or AA specifying the data it needs.
If accepted, the responding LEA or AA forwards this request to the CSP. HI1 standard defined by [2] may be used for such order towards the administrative entity of the CSP where the target is requested to be intercepted.
The CSP activates the request as a pure local request.
The CSP provides the intercepted data IRI and CC to the responding LEMF by using the already available HI’s (i.e. IP delivery HI’s based on TS 102 232 parts mechanism, ref. [3])
The responding LEMF sends data forward as IRI IW and CC IW in (near) real time to the requesting LEMF.
ETSI TC LI worked to define this latter step 5 interface by writing a new Technical Specification (TS) for Inter LEMF Handover Interface, ref. [4]. This work had significant support in ETSI by all members types (Government, Network operators, MF/DF system providers) and its 1st TS version was focused only on LI aspects.
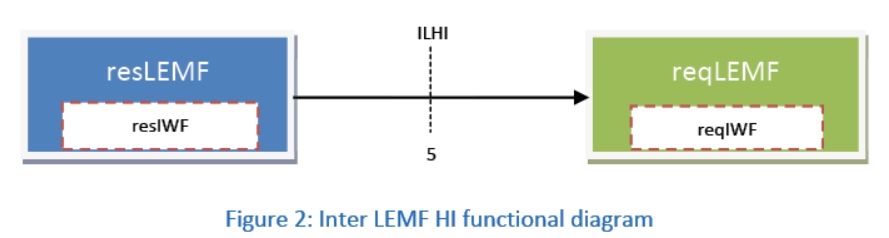
Figure 2 describes the functional diagram of this new HI, named ILHI, which supports the sending of LI data from the resLEMF and additionally the exchanging of all the control messages (e.g. error codes, keep alive messages) between resLEMF and reqLEMF. For data processing an Interworking function is defined for the resLEMF (resIWF) and for the reqLEMF (reqIWF). The resIWF shall process the data to provide interoperability while the reqIWF processes the data received over ILHI into local format as needed. The resIWF is structured into the three main functions of Mapping (MapF), Interoperability (IopF) and Encapsulation (EcsF) which all manage the LI data received from the CSP to create the PS-PDU with ILHI Payload.
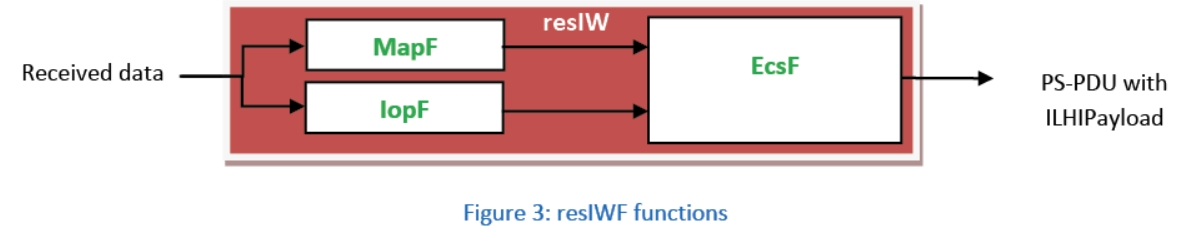
MapF is optional with resLEMF deciding if and how it is used to generate a mapping from every element of a given set to a distinctive element of another set (e.g. Timestamp and Location information).
IopF shall generate the res Payload in accordance to TS 102 232 family when the CSP Received data is not using ETSI TS 102 232 and forward it in addition to the received data sent as original Payload to the EcsF. If the received data from CSP is already according to TS 102 232 format, IopF shall only deliver it as res Payload to EcsF.
EcsF manages the data provided by MapF and IopF to create the ILHI Payload which has been defined by ETSI [4] by re-using existing standard HI’s TS 102 232 part 1 to 7 [3]. For the network layer, ILHI is proposed with two distinctive data flows (IRI and CC) using public Internet IP-VPN interconnection of the involved LEMFs or network connection secured by other means.
The new ILHI standard [4] resulted in greater efficiency and reduced impact on all parties concerned. A 2nd ILHI version has already been planned to provide Retained Data (RD) handover based on the ETSI TS 102 657 modelling. ©
Other articles of Gerald McQuaid
 ETSI LI & RD Status (Sept. 2019) -
ETSI LI & RD Status (Sept. 2019) - by Gerald McQuaid and Domenico Raffaele Cione (N. III_MMXIX)
This article highlights the relevant ETSI activity on Lawful Interception (LI) and Retained Data (RD) as update to the previous article of February 2017. The 2018th and 2019th period work items are described in the following section.
 LAWFUL INTERCEPTION IN VIRTUALIZED NETWORKS (Sept. 2017) -
LAWFUL INTERCEPTION IN VIRTUALIZED NETWORKS (Sept. 2017) - by Gerald McQuaid and Domenico Raffaele Cione (N. III_MMXVII)
NFV refers to the replacement of traditional specialised hardware devices with software that can be installed on standardised, off-the-shelf piece of hardware. ETSI work on NFV was initially set to address a requirement to define a list of base security requirements imposed by lawful interception in the NFV architecture.
 ETSI LI & RD Status (Feb. 2017) -
ETSI LI & RD Status (Feb. 2017) - by Gerald McQuaid and Domenico Raffaele Cione (N. I_MMXVII)
Current ETSI activity on Lawful Interception (LI) and Retained Data (RD) is managed mainly by three main standardization committees: ETSI TC LI (the leading LI/RD group), TC CYBER and ISG NFV
 LEMF TO LEMF INTERFACE TO SUPPORT EUROPEAN INVESTIGATION ORDERS (EIOs) -
LEMF TO LEMF INTERFACE TO SUPPORT EUROPEAN INVESTIGATION ORDERS (EIOs) - by Gerald McQuaid and Domenico Raffaele Cione (N. IV_MMXVI)
Imminently, the Directive 2014/41/EU of the European Parliament and of the Council of 3 April 2014 regarding the European Investigation Order (EIO) in criminal matters [1] is expected to become part of the EU-nations’ national laws. This EU directive requires each European Member State to transpose the directive into national law by 22 May 2017 (Article 33). This EIO describes the possibilities about lawful interception (LI) of telecommunications and collection of traffic and location retained data (RD) extended to network scenarios out of a pure national network context: an EIO may be issued for the interception of telecommunications by a Member State to obtain intercepted data of a target when using a communication service in a CSP’s network located in another Member State country (ref. Article 30 of [1]).
 THE LI-INTERFACE FOR WARRANT INFORMATION -
THE LI-INTERFACE FOR WARRANT INFORMATION - by Gerald McQuaid and Domenico Raffaele Cione (N. III_MMXVI)
Traditionally the ETSI standardization work was focused on IRI and CC data details by defining, updating and maintaining related data Handover Interfaces (HI-2 and HI-3) specifications. Furthermore, ETSI had defined a dedicated Handover Interface, named HI-1, referred to be also crossing borders between countries based on corresponding international laws or agreements. HI-1 was defined as an interface between LEA and CSP to transport all kind of administrative information being used for the transmission of the request to establish or to remove the interception action from the LEA to the CSP and the acknowledgement message back to the LEA.
 Lawful interception items for VoLTE -
Lawful interception items for VoLTE - by Gerald McQuaid and Domenico Raffaele Cione (N. II_MMXVI)
VoLTE, Voice over Long Term Evolution (LTE), is a standard-based technology used to support voice calls over the LTE technology being now used by 4G wireless networks.
 ETSI AND STATUS OF LI & RD STANDARDS -
ETSI AND STATUS OF LI & RD STANDARDS - by Gerald McQuaid and Domenico Raffaele Cione (N. I_MMXVI)
This thematic section is intended to inform readers on the latest progress of standardization work items on Lawful Interception (LI) and Retained Data (RD) mainly focusing on European regional level (ETSI). The scope is to cover all relevant LI and RD aspects in terms of requirements, communication service providers architecture and network interfaces/protocols definition.
 Gerald MCQUAID - Chairman of ETSI Technical Committee for Lawful Interception and attending ETSI TC CYBER and 3GPP SA3 LI since 2004. Member of the EU Data Retention Experts Group under the auspices of the European Commission.
Gerald MCQUAID - Chairman of ETSI Technical Committee for Lawful Interception and attending ETSI TC CYBER and 3GPP SA3 LI since 2004. Member of the EU Data Retention Experts Group under the auspices of the European Commission.Other articles of Domenico Raffaele Cione
 ETSI LI & RD Status (Dec. 2022) -
ETSI LI & RD Status (Dec. 2022) - by Domenico Raffaele Cione (N. IV_MMXXII)
This document highlights the ETSI activity on Lawful Interception (LI) and Retained Data (RD) at end of 2022 as update from Q4 2021 status.
 ETSI LI & RD Status (Dec. 2021) -
ETSI LI & RD Status (Dec. 2021) - by Domenico Raffaele Cione (N. IV_MMXXI)
This document highlights the ETSI activity on Lawful Interception (LI) and Retained Data (RD) at end of 2021 as update from Q4 2020 status.
 ETSI LI & RD Status (Dec. 2020) -
ETSI LI & RD Status (Dec. 2020) - by Domenico Raffaele Cione (N. IV_MMXX)
This article highlights the ETSI activity on Lawful Interception (LI) and Retained Data (RD) as update to the previous article of September 2019.
 ETSI LI & RD Status (Sept. 2019) -
ETSI LI & RD Status (Sept. 2019) - by Gerald McQuaid and Domenico Raffaele Cione (N. III_MMXIX)
This article highlights the relevant ETSI activity on Lawful Interception (LI) and Retained Data (RD) as update to the previous article of February 2017. The 2018th and 2019th period work items are described in the following section.
 LAWFUL INTERCEPTION IN VIRTUALIZED NETWORKS (Sept. 2017) -
LAWFUL INTERCEPTION IN VIRTUALIZED NETWORKS (Sept. 2017) - by Gerald McQuaid and Domenico Raffaele Cione (N. III_MMXVII)
NFV refers to the replacement of traditional specialised hardware devices with software that can be installed on standardised, off-the-shelf piece of hardware. ETSI work on NFV was initially set to address a requirement to define a list of base security requirements imposed by lawful interception in the NFV architecture.
 ETSI LI & RD Status (Feb. 2017) -
ETSI LI & RD Status (Feb. 2017) - by Gerald McQuaid and Domenico Raffaele Cione (N. I_MMXVII)
Current ETSI activity on Lawful Interception (LI) and Retained Data (RD) is managed mainly by three main standardization committees: ETSI TC LI (the leading LI/RD group), TC CYBER and ISG NFV
 LEMF TO LEMF INTERFACE TO SUPPORT EUROPEAN INVESTIGATION ORDERS (EIOs) -
LEMF TO LEMF INTERFACE TO SUPPORT EUROPEAN INVESTIGATION ORDERS (EIOs) - by Gerald McQuaid and Domenico Raffaele Cione (N. IV_MMXVI)
Imminently, the Directive 2014/41/EU of the European Parliament and of the Council of 3 April 2014 regarding the European Investigation Order (EIO) in criminal matters [1] is expected to become part of the EU-nations’ national laws. This EU directive requires each European Member State to transpose the directive into national law by 22 May 2017 (Article 33). This EIO describes the possibilities about lawful interception (LI) of telecommunications and collection of traffic and location retained data (RD) extended to network scenarios out of a pure national network context: an EIO may be issued for the interception of telecommunications by a Member State to obtain intercepted data of a target when using a communication service in a CSP’s network located in another Member State country (ref. Article 30 of [1]).
 THE LI-INTERFACE FOR WARRANT INFORMATION -
THE LI-INTERFACE FOR WARRANT INFORMATION - by Gerald McQuaid and Domenico Raffaele Cione (N. III_MMXVI)
Traditionally the ETSI standardization work was focused on IRI and CC data details by defining, updating and maintaining related data Handover Interfaces (HI-2 and HI-3) specifications. Furthermore, ETSI had defined a dedicated Handover Interface, named HI-1, referred to be also crossing borders between countries based on corresponding international laws or agreements. HI-1 was defined as an interface between LEA and CSP to transport all kind of administrative information being used for the transmission of the request to establish or to remove the interception action from the LEA to the CSP and the acknowledgement message back to the LEA.
 Lawful interception items for VoLTE -
Lawful interception items for VoLTE - by Gerald McQuaid and Domenico Raffaele Cione (N. II_MMXVI)
VoLTE, Voice over Long Term Evolution (LTE), is a standard-based technology used to support voice calls over the LTE technology being now used by 4G wireless networks.
 ETSI AND STATUS OF LI & RD STANDARDS -
ETSI AND STATUS OF LI & RD STANDARDS - by Gerald McQuaid and Domenico Raffaele Cione (N. I_MMXVI)
This thematic section is intended to inform readers on the latest progress of standardization work items on Lawful Interception (LI) and Retained Data (RD) mainly focusing on European regional level (ETSI). The scope is to cover all relevant LI and RD aspects in terms of requirements, communication service providers architecture and network interfaces/protocols definition.
 Domenico Raffaele CIONE - Active delegate in ETSI Technical Committees for Lawful Interception (LI) and Retained Data (RD) since 2003
Domenico Raffaele CIONE - Active delegate in ETSI Technical Committees for Lawful Interception (LI) and Retained Data (RD) since 2003 ETSI LI & RD Status (Dec. 2022)
ETSI LI & RD Status (Dec. 2022) ETSI LI & RD Status (Dec. 2021)
ETSI LI & RD Status (Dec. 2021) ETSI LI & RD Status (Dec. 2020)
ETSI LI & RD Status (Dec. 2020) ETSI LI & RD Status (Sept. 2019)
ETSI LI & RD Status (Sept. 2019) Le innovative tecniche di sopralluogo e ricostruzione 3D applicate al cold case dell’omicisio di Poli Valeriano
Le innovative tecniche di sopralluogo e ricostruzione 3D applicate al cold case dell’omicisio di Poli Valeriano