Ing. Fabio ROMANI and Dr Yassine FATAH
 Ing. Fabio ROMANI is Chief Executive Officer of IPS S.p.A, a leading company in the Cyber Intelligence sector. IPS operates in more than 20 Countries aiding Law Enforcement Agencies and Police Departments on a daily basis.
Ing. Fabio ROMANI is Chief Executive Officer of IPS S.p.A, a leading company in the Cyber Intelligence sector. IPS operates in more than 20 Countries aiding Law Enforcement Agencies and Police Departments on a daily basis.Dr. Yassine FATAH, Product Specialist of IPS S.p.A and Instructor for IPS Academy. The Academy hosts more than one hundred training days and advanced technical lessons for thousands of Police Officers every year.
The ever-growing use of the internet in the telecommunication domain drives to a new technological and investigative approach toward the integrated exploitation of metadata. Live Deep Packet Inspection systems gain more and more centrality when compared to the past in the integrated modern view of doing an investigation.
Among the investigative methodologies, the internet traffic analysis has always been marginal compared to the more traditional ones. Historically, this technology has proved to be effective less often compared to others due to the always diminishing expenditure in R&D by Intelligence sector companies. In addition to this, the concern rising about the security and privacy of users led the standard of encryption to a higher level nowadays leading LEAs toward a more active data collection approach.
The solution offered by an active method of interception such as the Software Agent is particularly attractive considering that in order to decrypt information secured by TLS/SSL with modern computers would take more than a thousand years. Being ahead of the encryption game is pivotal in ensuring success, but it is not always possible due to the natural limitations carried by the direct interaction with the target’s device.
The use of such software is getting more and more difficult due to some implications:
- Google and Apple security concerns to keep their operating systems invulnerable
- The leaks of the social engineering techniques used to inject the devices
- A normative framework that leaves some grey areas
Considering what is mentioned above, this article is to be considered as a walkthrough over the metadata extraction technology using a passive approach and how today it is crucial in the modern criminal fighting scenario. The intent of this article is to demonstrate that broader use of this technology would be beneficial even to those investigators with fewer skills in the IT domain.
In the last decade, all kind of telecommunication has shifted to the Internet. Messaging apps provide a stable, free and reliable VoIP (Voice over IP) alternative to the GSM. Furthermore, also Telcos are using the internet for their Voice over LTE (VoLTE), and with the arrival of the 5G each and every type of communication between people and machines (IoT) will use the internet.
In some investigative context, it is safer to keep the distance from the target and stay eclipsed to observe the activity from the window trying to catch information that the target itself provides (checking the trash bin for instance) rather than entering the room to be able to listen to their conversation. Following the same concept, being passive but constantly on the network might yield eventually taking advantage of the vulnerabilities that the network still exposes us.
Going in dept of what extracting metadata means, let’s consider any messaging application. Analyzing the data flow of a device that is using for instance WhatsApp, quite a few valuable pieces of information can be rebuilt using heuristic algorithms. Through an advance and complex mechanism, it is possible to construct a Social Calls CDR (Call Detail Records) with the following Metadata:
- Application Used (WhatsApp, Telegram, Messenger, Etc.);
- Type of event (Call, Video Call, Chat, Etc.);
- Duration of the event;
- Time reference;
- Unique ID of the Target;
- Unique ID of the Interlocutor;
- ISP of the Interlocutor.
The above list shows that the metadata extraction with a passive perspective, might provide valuable information of the target, but also of the people interacting with them.
We now analyze the data path of a WhatsApp text message and later the data path of a WhatsApp call.
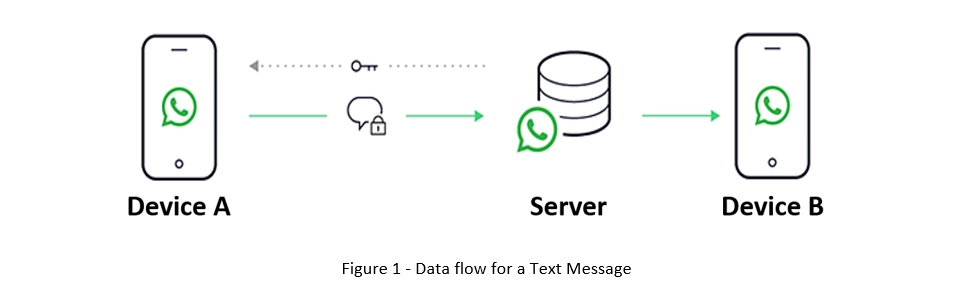
WhatsApp Text Message:
- Text message sending from device A to device B
- The message reaches the Provider Server
- The message is redirected toward device B
- Device A receives a confirmation of receipt from the Server
- The process restart in case of device B replying
In this case scenario, intercepting the internet traffic of device A would result in a series of encrypted connections to the servers of the provider (WhatsApp).
WhatsApp Social Call:
The route followed by data on a Call it differs substantially:
- Device A calls device B
- The query reaches the Server that forwards the call to device B
- If device B replies, direct communication is disposed
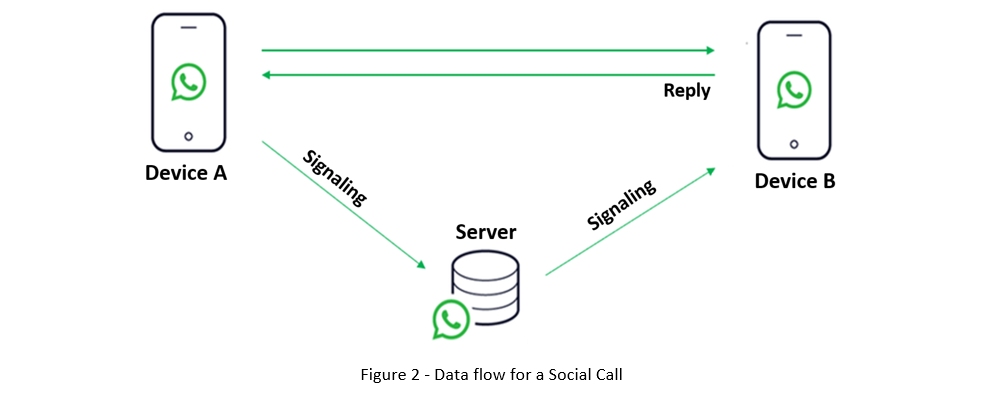
From the Server workload and quality perspective, direct communication is way more efficient. Knowing the structural logic behind the protocol it is possible to highlight a few valuable metadata. The unique IDs, alongside the time of the call are sufficient to determine the specific device used by the interlocutor. This information is used to reconstruct the identity and location of a person of interest.
The enrichment of such IDs, extracted from the CDR, can lead to a more complete and omni comprehensive identification of the people involved in the case. The enrichment could bring the following parameters:
- Phone number;
- Accountholder;
- IMSI;
- IMEI;
- BTS as in Cell Tower Antenna.
The investigative aspects deriving from the above are many. For instance, there might be the chance to link a conversation captured through an environmental interception to two identities that become certain and certified from the Telco Operator after the Metadata enrichment. Furthermore, the investigator could grasp the destination of a Call that is considered as secured by the terrorist or by the affiliate of an international criminal organization.
There are some key elements that must be taken into consideration in the balance of cost benefits. Hence, the passive interception applying a metadata extraction is on the one hand a transparent technique, with the target unaware of the ongoing interception and on the other hand, the data collected are irrefutable and undeniable before the Court as the data enrichment comes for the Telco itself.
The Passive interception system with metadata extraction capabilities proposed by IPS, GENESI IP analyzer, is based on a technology that enables multiple operative uses (also unconventional). Indeed, GENESI might be used also offline to analyze imported Dump coming from multiple sources. For example, during a tactical operation, the operator can “Sniff” the Wi-Fi traffic and import the result into GENESI. Furthermore, the operator can install a probe in a specific place to intercept a trunk of the network. To conclude one can also import Pcap Files that have been intercepted using other vendors’ systems.
Alongside the functionalities discussed so far, more can be highlighted:
- Identifying how many and the typology of devices are connected to a certain network. This is valuable from an operational standpoint as knowing this might provide a higher chance of success in an intrusion activity. The same concept can be applied to a hotspot for other devices;
- Provide the list of Servers contacted by the people connected to the network and highlight a hostname list;
- With the use of an intuitive link analysis rebuilt the connections and reveal unclear dynamics;
- Keep records of the uploaded and downloaded traffic toward a specific service (a forum or the dark web or YouTube) to identify potential Targets dealing with Terrorism, Propaganda, or Pedophilia;
- Track the connection of Crypto Phones toward specific services (SkyECC, No1BC, Diamond Secure etc.) reporting the registering and network identification metadata.
This list above, which is not definitive, demonstrates how helpful this technology could be. The real potential of it can be reached when supported by (or in support of) other technologies such as telephonic interception. Having this in mind, the IPS system is currently used in most of the Italian Judiciary offices, it is used by the main Police forces on a daily basis and has been chosen by the Ministry of Interior as the leading platform in the Internet analysis.
In the ever-changing telecommunication world, the Internet is the key. For this reason, today using a groundbreaking tool like GENESI is becoming more and more decisive for investigative activity.
 Prestazioni obbligatorie sulle reti wifi
Prestazioni obbligatorie sulle reti wifi Servono certificatori per gli strumenti di intercettazione
Servono certificatori per gli strumenti di intercettazione Cyber Threat Intelligence: essential Intelligence methods and technologies for minimizing threats in the cyber realm
Cyber Threat Intelligence: essential Intelligence methods and technologies for minimizing threats in the cyber realm Prestazioni funzionali delle intercettazioni: bozza di decreto con grandi criticità tecniche
Prestazioni funzionali delle intercettazioni: bozza di decreto con grandi criticità tecniche